Xmlrpc.php can be exploited by hackers to gain access to a WordPress site. Therefore, it is recommended that you disable Xmlrpc in WordPress. WordPress has always had a way for you to log in remotely and take care of things on your site.
Sometimes, though, you’ll need to access your website from a place where your computer isn’t nearby like when you’re traveling. And that’s why the xmlrpc.php file has become kind of annoying instead of helpful. In this article, we’ll take a look at what xmlrpc.php actually is and why it was created.
We also go over how to fix the common security vulnerabilities it causes on your own WordPress site.

Table of Contents
What is Xmlrpc.php?
XML-RPC allows WordPress to send XML-encoded data to other systems over HTTP. Because WordPress isn’t a self-contained system, sometimes it needs to reach out to other systems, and XML-RPC was developed to handle that job.
For example, if you wanted to post to your site from a mobile device while away from your computer, You could use the xmlrpc.php remote access feature to do that.
Some of the key features that enabled xmlrpc.php were allowing you to connect to your site via smartphone to send trackbacks and pingbacks from other sites, and some functions associated with Jetpack.
What Was the Purpose of Xmlrpc.php and How Was It Used?
XML-RPC was included in WordPress when it was known as b2/cafelog. There was once a time when connections to the internet were extremely slow, web publishing was a tough process. people wrote and published using offline computers and then copied and pasted their content onto the web.
The solution was an offline blogging client that allowed users to write their content offline and then connect to publish it when they were ready. This connection was accomplished through XML-RPC, a web service protocol. Early applications using this protocol allowed users to log into their WordPress accounts from other devices.
Xmlrpc at Present
In 2008, version 2.6 of WordPress introduced a new feature: the ability to enable or disable XML-RPC support. However, with the release of the WordPress iPhone app, which came out in 2010, the developer team decided to enable XML-RPC support by default, and there is no way to turn it off through the settings. This has remained true to this day.
However, the function of this file has changed over time and it has been reduced in size from 83kb to 3kb. As a result, it plays a smaller role than it used to.
Xmlrpc Future
The WordPress API has made it possible for XML-RPC to be entirely eliminated. Currently, in the trial phase, the development of this new API is only available through a plugin.
Although the XML-RPC API was developed to supplement the built-in WordPress function, we expect it to be built into the core soon, which will eliminate the need for xmlrpc.php altogether.
New API doesn’t like what people want, but it’s a lot better than the old one.
Why You Should Disable Xmlrpc
The biggest issues surrounding Xmlrpc have to do with security. An XML-RPC file can be used to launch a brute-force attack on your site, but it’s not the file itself that’s at fault for this; it’s the way it can be used.
You can protect your blog manually by creating strong passwords and installing security plugins. However, the best way to keep safe is to simply disable it.
Two main weaknesses of Xmlrpc have been exploited in the past. One method of attack is brute-force password guessing. An attacker can try every possible username and password combination on your site by using a single command that tests hundreds of different passwords. The hackers can do this with a single line of code, which gets around security tools that block brute force attacks.
The second way was to create a massive DDoS attack by sending pingbacks to thousands of WordPress sites at once. A pingback is a method of communication between blogging platforms, so hackers could enlist the help of thousands of WordPress sites to send requests to your site. The xmlrpc.php feature in WordPress provided hackers a virtually limitless supply of IPs to attack with a DDoS.
To see whether Xmlrpc is running on your site, you can use a tool called Xmlrpc Validator. Enter your site into the tool and If you get an error message, then XML-RPC is either not enabled or your server isn’t responding.
If you receive a success message, you can disable Xmlrpc in WordPress with either of the two options shown below.
First Method: Disabling Xmlrpc
One method of disabling XML-RPC on your WordPress site is to use a plugin. To disable XML-RPC on your WordPress blog, navigate to Plugins › Add New from your dashboard. Enter Disable XML-RPC into the search box at the top of the screen, then install the plugin that looks like the image below.
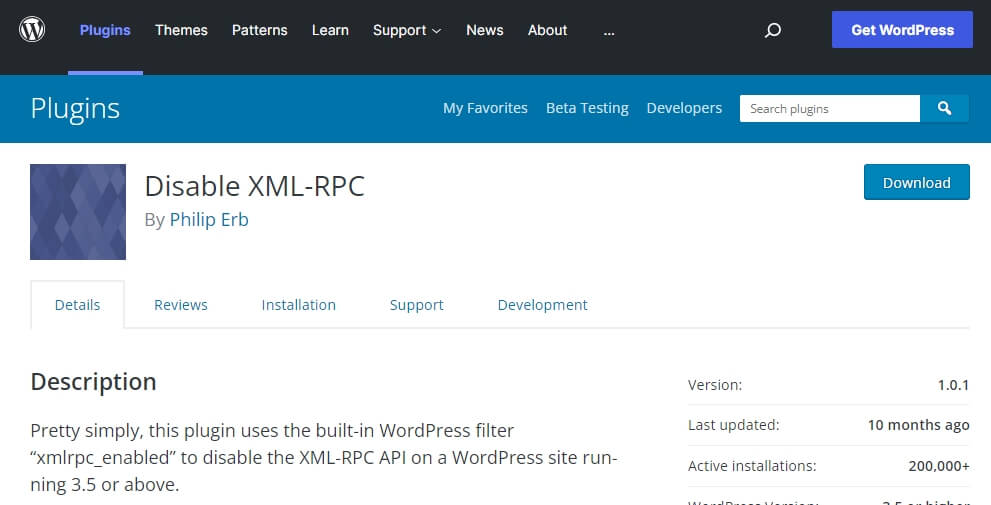
Activate the plugin and you’re good to go. The plugin will add the necessary code to disable XML-RPC.
But, keep in mind that some existing plugins may partially depend on XML-RPC functionality, so disabling it completely may cause a plugin conflict or some of the site’s functionality will be lost.
If you’d like to disable XML-RPC but still, use specific plugins and features, then the following plugins disable them:
Stop Xmlrpc Attack: This plugin will block all Xmlrpc attacks, This plugin is designed to block all Xmlrpc attacks.
Control Xmlrpc Publishing: You can retain control and use the xmlrpc.php remote publishing option by using.
Second Method: Disabling Xmlrpc.php Manually
If you prefer to do it manually, follow this approach to prevent unauthorized xmlrpc.php requests from being processed.
Open the .htaccess file in your web browser. To find this file, you might need to enable the ‘show hidden files option in your file manager or FTP client.
Insert the following code in your .htaccess file,
# Block WordPress xmlrpc.php requests <Files xmlrpc.php> order deny,allow deny from all allow from xxx.xxx.xxx.xxx </Files>
Important! Replace xxx.xxx.xxx.xxx with the IP address that should be allowed access to xmlrpc.php.
Fix 7 Common WordPress Errors
If you’re looking for more tips on how to fix WordPress errors, we’ve got you covered. Check out our following post on common WordPress errors and how to fix them.
-
- How to Fix Internal Server Error 500
- How to Fix Syntax Errors in WordPress
- How to Fix the WordPress White Screen of Death
- How To Fix The Image Upload Issue In WordPress
- How to Fix The WordPress Memory Exhausted Error
- How to Fix the Error Establishing a Database Connection in WordPress
- How to Fix Briefly Unavailable for Scheduled Maintenance Errors in WordPress
Final Thoughts: Disable Xmlrpc in WordPress
Overall, Xmlrpc.php is a good solution to some of the issues that may arise when publishing to your WordPress site remotely. There are some security issues with this feature, though, that you should be aware of.
To keep your site safe, it’s a good idea to disable the xmlrpc.php file entirely. Unless you need some of the functions needed for remote publishing or if you use the Jetpack plugin, you can prevent vulnerability by using a security patch plugin.
We can expect the features of Xmlrpc.php to be integrated into WordPress in time. This will allow remote access without compromising security. However, until then, you should protect yourself from potential Xmlrpc.php security holes.
Have you ever blocked Xmlrpc.php access to your WordPress site, either through a plugin or manually? We’d love to hear about your experience in the comments below. If you like this article share it on social media.







